Indeed, in the advanced technology these days, we cannot run away from technology, people are getting smarter in creating techonologies that help us in future. Now, Malaysia is using Touch n Go to use in toll transactions and parking lots.
However, compare to Singapore, EZ-link has been successfully implement in its country. How about Malaysia? It looks like Malaysia need more time in applying these advanced technologies where we no need to bring cash but just bringing a card along with us and we can eat,shop,doing health care, drink coffee.
Touch n Go has been an easy card for us as consumers. It indeed help us a lot in our daily lives. If one day Touch n Go card can be used in buying fast food, I will be the first person glad for it.
Till then , if only Malaysia standardized whole country using only one card, or treat the card like debit card, hence I feel consumers will for sure buy Touch n Go card for it can be use at anywhere else.
Sources:
http://www.ezlink.com.sg/whereEzlinkUsed.htm
Monday, June 30, 2008
Review on Using Touch n Go card to buy fast food in Malaysia will be a reality
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/30/2008 02:37:00 AM 0 comments
Credit Cards Debts :Causes & Prevention
Do you have a credit card? How did you use it?
 Causes:
Causes:Recently many people are suffering a lot debt due to inappropriately use of credit card. Several reasons make them face such the kind of problems, for example they have a poor management in their money spending. Many people always prefer not to do any money planning before they spend their money, this may cause them over budget or may be buy something that are unnecessary in their daily life. When the end of the month is around the corner, they will only realize that their spending is too much and they need to clear a big amount for the credit card. Of course it will automatically become a big debt for them. Secondly, people like to use credit card to buy what they are like because they like to enjoy the luxury life. When due date of the credit card payment, they unable to pay the payment, they will go and register other credit card to cover the payment. This process continue repeated, user will loss their self control and make them continue to pay the interest and the amount of debt will become bigger and bigger.
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/30/2008 02:19:00 AM 0 comments
Mobile Payment System in Malaysia ~~MMWallet
WHat iS MOBile PAyMEnt ??!!
Mobile payment is the collection of money from a consumer via mobile devices such as mobile phone, SmartPhone, Personal Digital Assistant (PDA), wireless tablets and other devices. That using GPRS and wireless system build in the phone to access internet.
A mobile payment or m-payment may be defined as any payment where a mobile device is used to initiate, authorize and confirm an exchange of financial value in return for goods and services. The realization of mobile payments will make possible new and unforeseen ways of convenience and commerce.
How Does It Works??

is the current Mobile Payment System that available in Malaysia. Mobile Money is a PIN-based Mobile Payment Solution designed by Mobile Money International Sdn Bhd to address the limitations and bottlenecks created by cash, cheques and credit cards. MMWallet allow registered users to pay for goods and services at anytime, anywhere using only a mobile phone. Therefore, shoppers are freedom to buy products online and pay the merchant using mobile phone without physically present at the store.
Customer Adoption Strategies
Mobile Payment indeed offers consumers financial freedom and independence without having to carry cash or fits the needs for those who do not have a traditional bank account. To encourage mobile payment in use in Malaysia, the company should advertise their mobile payment system to others, as we are into the advanced techonology year. Hence, attracting consumers with the benefit of having mobile payment, by just bringing their mobile phone can make any transcation.
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/30/2008 12:44:00 AM 0 comments
Sunday, June 29, 2008
The Application of Pre-Paid Cash Card For Consumers
Prepaid cash card is an electronic cash cards. There are some differences from credit card and debit card. As their name indicates, prepaid cash cards have been pay in advance. Prepaid cash card need personal identification number to make transaction, thus you no need worry when someone steal your information.
Example : Octopus Card


Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/29/2008 11:27:00 PM 0 comments
Monday, June 23, 2008
Review on the post "New Spamming Tactics"
In my opinion, using spam filter is not a very good option. The chances of successfully filter out the spam is not guarantee, at the same time it may accidently filter out your important mail.
The best way of avoiding spam is not to open any suspected mail. An important mail or official messages from companies always have proper mail title and sender name where immiately tell you what is the content about.
Most importantly, stop forward the spam mail around. For example, “MSN is full…, Please reverting this message to keep you account live…. Etc”. Mail service provider as well as other web site will never delete user account.
I appreciate Mr.Hen bring out the tactic of using PDF spam. I never thought of this as spam before I read this post. In addition to this, some malicious software make use of “.zip.exe, .doc.exe, .xls.exe” to trick their victims.
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/23/2008 01:53:00 AM 0 comments
Sunday, June 22, 2008
How Safe Is Our Data??
Just about anyone that gets online is at risk!!!
Online security threats are one of the biggest challenges on the Internet today.
Want to know what are the threats are heading your way ? Here, we bring you the updates on the viruses.
Cyber attacks fall under several categories, accidental actions and malicious attacks. Under this, there also include computer viruses, denial of service attacks and distributed denial ofservice attacks. Thus, identity theft and data theft also included.MySpace, Facebook has been the primary attack of the hackers.
- Accidental Actions
¤This category encompasses problems arising from lack of knowledge about online security concepts such as poor passwords choices, business transactions and outdated software

- Malicious Attacks>
¤ Attacks that specifically aim to do harm which can be further broken down into attacks will caused intential misinterpretation. Malicious code, on the other hand, so called "cracking" and "hackings"
- Denial Of Service Attacks
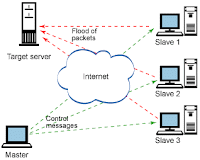 >
>
¤ Denial of service attacks, another form of malicious code, are carefully craftedand executed. Distributed DoS is a type of attack used on popular sites, such as Yahoo!®. In this type of attack, the hacker infects computers on the Internet via a virus or other means. This attack not only causes the target site to experience problems, but also the entire Internet as the number of packets is routed via many different paths
to the target. - Data Theft
>
¤ Data theft over the Internet has dramatically increased in recent years. There have already been around one hundred known cases around the world in which 40 million credit cards numbers have been stolen. Many card providers now have added security and software designed to protect credit card holders. One example is The Falcon, fraud detection software that watches all accounts constantly, looking for irregularities, such as unusually large transactions, irregular spending or simultaneous purchases in two different places. - Trojan Horse
>
¤ The file infector which means the virus will attach with other files when you’re running it in your computer. The threats can destroy the computer functions and significant information even can spoil the device of the computer.
Sources :
http://www.businessweek.com/technology/content/nov2007/tc2007119_234494.htm
http://www.ibm.com/developerworks/websphere/library/techarticles/0504_mckegney/0504_mckegney.html http://www.buzzle.com/articles/different-types-of-computer-viruses.html
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/22/2008 11:24:00 AM 0 comments
Saturday, June 21, 2008
Phishing: Examples and its Prevention Method
 Phishing is the process of attempting to criminally and fradulently acquire sensitive information, such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic communication. Pay Pal, eBay ,MSN, Yahoo and online banks are common targets.
Phishing is the process of attempting to criminally and fradulently acquire sensitive information, such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic communication. Pay Pal, eBay ,MSN, Yahoo and online banks are common targets.
How phishing works?
The perpetrator carried out using email addresses and instant messaging. They will use fake website they have created instead of legitimate one to entice people to share sensitive information, like usernames, password and credit-card details.
Examples :
 1. The "From Field" appears to be from the legitimate company mentioned in the e-mail. It is important to note, however, that it is very simple to change the "from" information in any e-mail client.
1. The "From Field" appears to be from the legitimate company mentioned in the e-mail. It is important to note, however, that it is very simple to change the "from" information in any e-mail client.
2. The e-mail will usually contain logos or images that have been taken from the Web site of the company mentioned in the scam e-mail.
3.The e-mail will contain a clickable link with text suggesting you use the inserted link to validate your information. In the image you will see that once the hyperlink is highlighted, the bottom left of the screen shows the real Web site address to which you will go. Note that the hyperlink does NOT point to the legitimate Citibank Web site URL
Prevention Method
- Guard against spam
ゅBe especially cautious of emails that, come from unrecognized senders.Which ask you to confirm personal or financial information over the Internet or make urgent requests for this information.
ゅTry to upset you into acting quickly by threatening you with frightening information. - Do not click on links, download files or open attachments in emails from unknown senders. ゅIt is best to open attachments only when you are expecting them and know what they contain, even if you know the sender
- Check your online accounts and bank statements regularly to ensure that no unauthorized transactions have been made
- "Dear Valued Customer."
ゅPhishing e-mail messages are usually sent out in bulk and do not contain your first or last name. Although, it is possible that con artists have this information. Most legitimate companies (but not all) should address you by first and last name. - Beware of pop-ups
Never enter personal information in a pop-up screen.
ゅDo not click on links in a pop-up screen.
ゅDo not copy web addresses into your browser from pop-ups.
ゅ Legitimate enterprises should never ask you to submit personal information in pop-up screens, so don’t do it. - Immediately Report Suspected Phishing Contacts
ゅ If you do receive a message you suspect to be a phishing scam, call the customer service phone number right away to confirm whether you've received an actual message or not. In addition, almost every bank and credit card lender has a website where you can report suspicious emails and instant messages.
Sources
http://www.webopedia.com/didyouknow/internet/2005/phishing.asp
http://www.msun.edu/infotech/its/how/security/phishing-examples.htm
http://www.spywareremove.com/phishing/preventphishingscams.php
http://www.identitytheftkiller.com/prevent-phishing-scams.php
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/21/2008 08:06:00 PM 0 comments
How to Safeguard Our Personal and Financial Data?
Why should we safeguard???
Having the thought of ,the personal data and your financial data being exposed to others. Who knows, some one will just hack your account or computer to steal all the information?
It is crucial that we have steps to guide us to prevent all these happened.
How do we prevent these?
- Use and maintain anti-virus software and a firewall
- Clear your browser cookies after every session.
default.Change your local username daily. Browsers and other software have been known to pass local
- Regularly scan your computer for spyware
- Avoid accessing financial information in public
>How can you tell if your financial site is really secure before you log on? The Web address should start with "https," instead of "http," says Weston. Also, look for small lock icon in the lower-right corner of the browser window.
- Password
 >Coming up with and storing secure passwords to protect the personal financial data. Like choose the passwords that would be difficult for someone who can figure out, do not use personal information, and keep a record of important passwords that guard financial data
>Coming up with and storing secure passwords to protect the personal financial data. Like choose the passwords that would be difficult for someone who can figure out, do not use personal information, and keep a record of important passwords that guard financial data
Sources:
http://gigaom.com/2007/12/26/how-to-safeguard-your-privacy-online/
http://finance.yahoo.com/banking-budgeting/article/103893/Six-Ways-to-Safeguard-Your-Online-Assets
http://cordis.europa.eu/ictresults/index.cfm/section/news/tpl/article/BrowsingType/Features/ID/88408
http://www.us-cert.gov/cas/tips/ST06-008.html
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/21/2008 06:07:00 PM 0 comments
Sunday, June 15, 2008
Ways E-Commerce can reduce cycle time, improve employees' empowerment and facilitate customer support
E-Commerce Reduce Cycle Time
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/15/2008 03:38:00 PM 0 comments
The History and evolution of E-Commerce
It is the online transaction of business which links the computer system with vendor, host and buyer thus also transfers of ownership or rights to use a good or service. The most famous activities on the Web are shopping. Everyone can shop everywhere and every time when online.
History of E-Commerce
History of ecommerce dates back to the invention of the very old notion of “sell and buy”, electricity, cables, computers, modems, and the Internet. Ecommerce became possible in 1991 when the Internet was opened to commercial use. Since that date thousands of businesses have taken up residence at web sites.
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/15/2008 12:55:00 PM 0 comments
Saturday, June 14, 2008
Breakdown of Kozmo and Causes
 Kozmo.com was founded in New York City in 1997 by Joseph Park, Kozmo began as a timeserving for harried customers. Kozmo, is a business with a new measure of instant consumer gratification- "to deliver every order in less than an hour". It satisfy customers needs whether is an ice-cream or a book thus also the first dot-coms to promise online deliveries.
Kozmo.com was founded in New York City in 1997 by Joseph Park, Kozmo began as a timeserving for harried customers. Kozmo, is a business with a new measure of instant consumer gratification- "to deliver every order in less than an hour". It satisfy customers needs whether is an ice-cream or a book thus also the first dot-coms to promise online deliveries.What causes Kozmo To Fails??
1.Unable to Develop Brand
Kozmo was unable to create brand image that was much different from that of a convenience store on wheels. Kozmo lacked the integration of customer needs, a brand that communicated an ability to satisfy those needs
2. Expanded its business too fast
Rapid expansion and intensive spending to gain market share and brand recognition. Amazon.com, Softbank Capital Partners, Chase Venture Capital, Oak Investment Partners, Flatiron Partners, Liberty Digital and J. & W. Seligman. Starbucks was also an early investor.

3. High expectation on the business
Use the Internet to combine the convenience of a catalog with the immediate gratification of in stores hopping by offering entertainment, food, and convenience products delivered within one hour, with no minimum order required and no delivery charges.
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/14/2008 05:52:00 PM 0 comments
Thursday, June 12, 2008
EBay Triumph and Causes
eBay is the biggest auction company online in the world. Due to the Internet becoming widely available inrecent years, online auctions have also become popular and more and more online auction suppliers entering this market.
What makes ebay as the top 5 success online auction company in the world?
Causes of the triumph of ebaY 1.Web Sites Design and Contents
1.Web Sites Design and Contents
Web site layout- layout must be clear, comfortableand easy to use, with good use of colour , typography and white space. Besides that, information architectures also can ease the users in browsing or finding particular item
 2. Give Great Customer Service
2. Give Great Customer ServiceInterative customer service and support feedback systems, email communication and toll free call. EbaY also provide answer center which include FAQs,auction listings,.These are the likelihood customers maintaining ongoing relationshops with ebaY.
3. Security
EbaY secure payment mechanism. This provides safer online shopping environment and minimizes risks to consimers. Hence personal information privacy which members' and online auction users' personal information has been secured and properly managed for authorised purposes only. Lastly, web site security which is an effective encrytionmechanism been adopted by ebaY for exchanging information, such as login information.
4. Consumer Education

Discussion boards which created for a particular topic that can attract and group those people who are interested in the topic and form an online community. Chat rooms, which ebaY also provides, it gives real-time and interactive communication for information exchange between members of the online community. This indeed has helped consumers on understand on the products that they want to buy.
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/12/2008 11:30:00 PM 0 comments
Thursday, June 5, 2008
Ourselves =) [The JYJ ]
 Myself =)
Myself =)Im Su-Yan, I am the youngest in the family, even though I didnt look like when in appearance. I have a dream, a dream to gain good result, to earn money for myself and take care of my family.But, the dream since getting farer than i suppose to be.
However ,back to the point of e-commerce, the website that i frequent surf are http://www.friendster.com/, http://www.thestar.com/, http://www.mail.yahoo.com/, http://www.sogua.com/ and http://www.jbtalks.cc/
Friendster, seems everyone using it, I use to make more friends and connect to people around the world. It helps a lot when you need some help from people who are in outstation.Example looking for journals articles for the thesis.
Yahoo mail, I use this to check my mails, eventually, now I have 1418 of inbox. It seems like I cannot read it all, maybe it will takes about 3 years to finish read it? Some times, the mail that I receive is really touching and I keep one for myself.
Myself ~~

Everyone have their own name, me also not excluded. My name is Wong Chee Seng; all my friends call me Jason. I am a year 3 semesters 1 student, from group 4 right now.
I have many hobbies such as swimming, jogging, playing badminton, playing computer games and surfing internet to search new information.
Normally the most website that I prefer to surf is www.gougou.com, www.Chinapress.com, www.Pbebank.com, www.googles.com, and also www.hotmail.com. Every website also can provide us with the information that we want to get for. For example, in the website of Gougou.com, I have the chance to search for many old and latest songs and also that latest movie, that’s why my life is always, entertain by this website.
Besides that, Chinapress.com can give me the chance to know about the latest news in Malaysia and also news from abroad country, by the way I can always save the money spending on the newspaper.
While the website like Pbebank.com really can save me a lot of time, it is because I can pay all my payment such as the electronic bill, water bill and also student bill without stepping out from my house. Beside that, my parent can easily transfer money to my account without going to bank. They just need to switch on the computer and press some button, and then all the process of transaction is successfully translated.
I usually view the Googles.com website to search for the information and pictures for my assignment and research.
The last website that I frequently surf is hotmail.com; I can send the messages to my friends and family without postman. It can save time and money to buy letter form. Through this website, I can check all my important mails which sent by others.
These several website really can help me so that I have no need to waste the time going out to search and get for the information, it really makes my life easier.
I come from Muar, Johor. The famous food in my hometown is “otak-otak”. If anyone wants to have a try the “otak-otak” can make appointment with me when you come. I will bring you the best and other foods.
During the free time, mostly I do are to watch drama and surf the web. The websites I will visit often are friendster, hotmail, baidu, orangeshark and sinchew. The purposes for me are to get know new friends, check mail, download songs, play games and know the latest news.
Posted by JYJ E-commerce [ Su-Yan * Jui Xiang * Chee Seng ] at 6/05/2008 09:54:00 PM 0 comments






