Just about anyone that gets online is at risk!!!
Online security threats are one of the biggest challenges on the Internet today.
Want to know what are the threats are heading your way ? Here, we bring you the updates on the viruses.
Cyber attacks fall under several categories, accidental actions and malicious attacks. Under this, there also include computer viruses, denial of service attacks and distributed denial ofservice attacks. Thus, identity theft and data theft also included.MySpace, Facebook has been the primary attack of the hackers.
- Accidental Actions
¤This category encompasses problems arising from lack of knowledge about online security concepts such as poor passwords choices, business transactions and outdated software

- Malicious Attacks>
¤ Attacks that specifically aim to do harm which can be further broken down into attacks will caused intential misinterpretation. Malicious code, on the other hand, so called "cracking" and "hackings"
- Denial Of Service Attacks
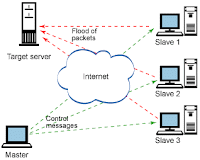 >
>
¤ Denial of service attacks, another form of malicious code, are carefully craftedand executed. Distributed DoS is a type of attack used on popular sites, such as Yahoo!®. In this type of attack, the hacker infects computers on the Internet via a virus or other means. This attack not only causes the target site to experience problems, but also the entire Internet as the number of packets is routed via many different paths
to the target. - Data Theft
>
¤ Data theft over the Internet has dramatically increased in recent years. There have already been around one hundred known cases around the world in which 40 million credit cards numbers have been stolen. Many card providers now have added security and software designed to protect credit card holders. One example is The Falcon, fraud detection software that watches all accounts constantly, looking for irregularities, such as unusually large transactions, irregular spending or simultaneous purchases in two different places. - Trojan Horse
>
¤ The file infector which means the virus will attach with other files when you’re running it in your computer. The threats can destroy the computer functions and significant information even can spoil the device of the computer.
Sources :
http://www.businessweek.com/technology/content/nov2007/tc2007119_234494.htm
http://www.ibm.com/developerworks/websphere/library/techarticles/0504_mckegney/0504_mckegney.html http://www.buzzle.com/articles/different-types-of-computer-viruses.html

0 comments:
Post a Comment